Most founders treat compliance as either a dead weight that crushes velocity or an afterthought – something to bolt on once the product is already scaling. Both are wrong and expensive. The companies succeeding in healthcare, finance, and legal services treat regulatory requirements as design problems, not paperwork. Not a department someone else owns. Design problems – the kind that, if you solve them early, give you a structural advantage your competitors can't easily replicate.
What happens when you don't treat them that way? TD Bank found out the hard way. In October 2024, the bank agreed to pay $3.1 billion to resolve allegations that it failed to maintain adequate anti-money laundering controls – the largest penalty ever imposed under the U.S. Bank Secrecy Act. The bank had left approximately $18.3 trillion in transactions unmonitored between 2018 and 2024, not because the technology to monitor them didn't exist, but because leadership had enforced a "flat cost" budget mandate that starved the compliance function of the resources it needed.
The Regulatory Terrain – Why It Feels Impossible
For technical decision-makers, the frustration with regulation isn't the law. It's translating statutes into production systems that actually work. Each domain has a different pressure point, and understanding where it sits is the first step toward building around it rather than against it.
Healthcare (HIPAA)
HIPAA requires a risk assessment to determine whether encrypting ePHI at rest and in transit is reasonable and appropriate. When encryption is needed, industry standards point to AES-256 at rest and TLS 1.2+ in transit. Organizations must either implement encryption, adopt an equivalent alternative, or document their reasoning for skipping both. In practice, encryption is reasonable for most environments, particularly cloud systems and remote access.
FinTech
The challenge here isn't the depth of any single regulation. It's the fragmentation. There is no unified federal money transmission regime in the United States. Instead, you navigate FinCEN registration, a hard gate that must be cleared before processing any transactions, and then a patchwork of 50+ individual state licensing jurisdictions. Each state is its own negotiation, with its own timeline. A 12-month engineering roadmap routinely becomes a 24-month compliance roadmap because of it.
LegalTech
LegalTech operates in a lighter regulatory environment than healthcare or finance, for now. But the EU AI Act and evolving state bar rules around the "unauthorized practice of law" are tightening the boundaries fast. The companies that will survive here are the ones building governance layers now: systems that can demonstrate algorithmic transparency and remain auditable for bias, before regulators make it mandatory.
How Good Intentions Fail – Three Case Studies
The cost of not architecting for compliance isn't theoretical. It shows up as fines, as failed launches, and as companies that simply disappear. Here are three cases that illustrate how this plays out.
Healthcare.gov: When the Schedule Becomes the Enemy
Healthcare.gov remains the sharpest illustration of what happens when timeline pressure collides with regulatory complexity. The Affordable Care Act was signed in 2010, but HHS delayed issuing final regulations until early 2013, partly for political reasons, leaving CMS and its contractors only months to develop and test a system of extraordinary complexity. The project had to integrate with the IRS, the Social Security Administration, and over 300 private insurance carriers across 36 states. End-to-end testing was compressed from the originally planned seven months to roughly one month before the October 1, 2013, go-live. The result was a national embarrassment: the site collapsed within hours of launch. The project was underfunded and poorly led, but the real issue ran deeper: regulatory timelines have hard floors you can't sprint past. If the architecture isn't ready, no amount of agile velocity will save you.
TD Bank and Sigma Broking: The Cost of "Set It and Forget It"
TD Bank's $3.1 billion settlement tells a story about chronic underinvestment, but the mechanism matters more than the headline number. According to the DOJ's plea agreement, the bank failed to substantively update its transaction monitoring system between 2014 and 2022, despite internal audits and federal regulators repeatedly flagging the gaps. Senior management knew. They chose a "flat cost paradigm", holding AML budgets flat year after year, over the investment required to keep pace with the bank's growth. The result: $18.3 trillion in transactions went unmonitored, and three money laundering networks moved over $670 million through TD Bank accounts.
Sigma Broking followed a similar trajectory on a smaller scale. In October 2022, the FCA fined the firm £531,600 for transaction reporting failures. The firm corrected the immediate violation but never built the monitoring infrastructure to detect whether the underlying problem had recurred. It did. By July 2025, the FCA imposed a second fine, this time £1,087,300, for the same category of failures spanning 2018 to 2023. Total regulatory penalties: over £1.6 million(approximately $2.22 million).
Both cases share the same mistake: fixing compliance problems once and then assuming they stay fixed, but they don't. Monitoring infrastructure needs to evolve with transaction volume.
2024 FCA Fines: Challenger Banks Caught Flat-Footed
In September 2024, the UK's Financial Conduct Authority fined Starling Bank £28.96 million (approximately $38.5 million) for sanctions screening failures so fundamental that the bank's automated system had been screening customers against only a fraction of the required sanctions list since 2017 — a misconfiguration that went undetected for six years.
Starling had also repeatedly breached an FCA requirement not to open accounts for high-risk customers, onboarding over 49,000 such customers between 2021 and 2023. Two months later, Metro Bank was fined £16.7 million (approximately $21 million) for failing to monitor over 60 million transactions due to a data-feed error in its automated monitoring system – an error that persisted from 2016 to 2020. Neither bank lacked a desire to comply. They lacked the architecture and, critically, the testing and oversight to prove they were complying.
The Architectural Shift – Five Principles That Change the Equation
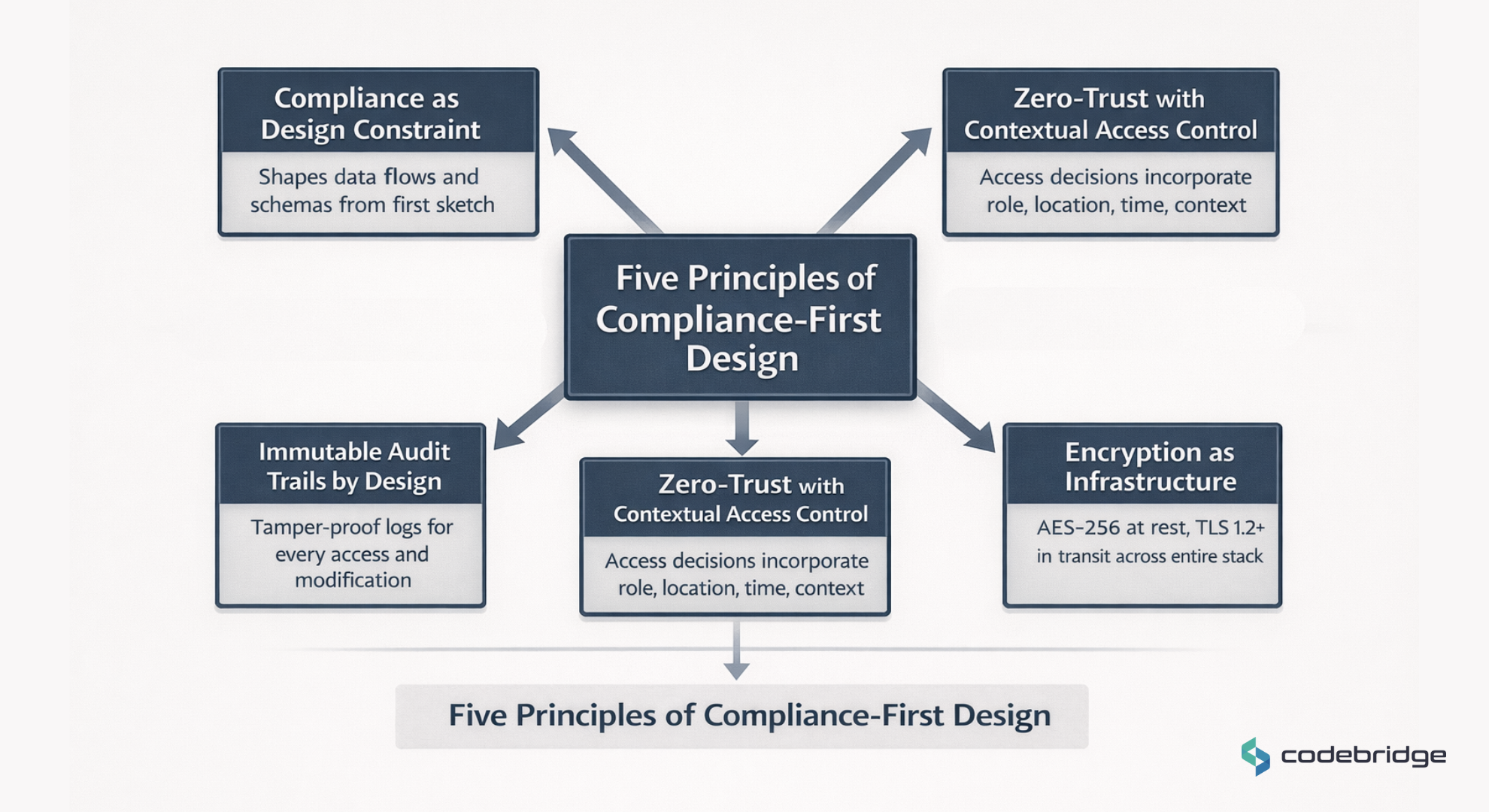
Reactive remediation is expensive. It's slow. And in regulated industries, it compounds, each patch creating new surface area for the next failure. The alternative is Compliance-First Design: building regulatory requirements into the system from the ground up, not bolting them on after the fact. Here's what that looks like in practice.
Principle 1: Compliance as a Design Constraint
Compliance must shape data flows, API contracts, and database schemas from the first sketch – not be layered on afterward. In HIPAA environments, this means encryption is part of how data moves, not a wrapper applied to an existing flow. In FinTech, transaction monitoring is native to how transactions are recorded, not a separate system reading from an external log.
Principle 2: Zero-Trust with Contextual Access Control
Many regulated organizations adopt Attribute-Based Access Control (ABAC) and zero-trust architecture as best practice, where access decisions incorporate role, location, time, and context. While not explicitly mandated by HIPAA or GDPR, ABAC aligns with principle-based requirements for 'appropriate technical controls.
Simple role-based access control (RBAC) is less sufficient for regulated systems but with compensating controls can also achieve compliance.
Principle 3: Encryption as Infrastructure, Not a Feature
AES-256 at rest and TLS 1.2+ in transit must be enforced across the entire stack — including internal microservices. Key management belongs in dedicated services (AWS KMS, Azure Key Vault, HashiCorp Vault), never hardcoded. And data minimization matters: the less data you collect and retain, the smaller your compliance footprint.
Principle 4: Immutable Audit Trails by Design
Every access to ePHI, every critical modification, every failed authentication attempt must be logged — and those logs must be tamper-proof. Append-only databases or object-lock policies in cloud storage close the assumption that logs can be altered. Regulators default to skepticism about log integrity. Immutability removes that skepticism entirely.
Principle 5: Policy as Code
Infrastructure as Code tools (Terraform, CloudFormation) combined with policy enforcement engines (Checkov, OPA) let you catch compliance drift before it reaches production. Non-compliant configurations are blocked at the CI/CD gate. The result is a version-controlled, auditable history of every infrastructure change – which is where compliance at scale actually lives.
The Role of AI and LLMs in Regulated Environments
AI adoption in healthcare and finance is accelerating faster than in almost any other sector. But the constraints on deploying generative AI in regulated environments are frequently misunderstood – and the gap between "AI works" and "AI works here" is where most companies get stuck.
Where LLMs Deliver Real Value
In healthcare, AI is already being deployed for clinical documentation — tools that transcribe doctor-patient conversations and generate structured notes, reducing the administrative burden that drives clinician burnout. In FinTech, AI-driven fraud detection identifies suspicious transaction patterns with lower latency than rule-based systems. In LegalTech, AI is transforming contract review: identifying risky clauses and summarizing case law at scale, tasks that previously required hours of manual work.
Where LLMs Break Down
The primary barrier to AI adoption in regulated industries isn't the model. It's the infrastructure around it. Hallucination – the tendency of LLMs to generate plausible-sounding but fabricated information – is catastrophic in high-stakes domains. A hallucinogenic drug interaction in healthcare can harm a patient. A fabricated legal precedent can lose a case. And standard LLMs trained on public data create a privacy risk if they ingest PHI or other protected information.
What "Getting It Right" Looks Like
Success in deploying AI in regulated environments requires a compliance-based approach to model selection and infrastructure. Enterprise platforms like OpenAI's healthcare offering now provide HIPAA support, signed Business Associate Agreements, and customer-managed encryption. It ensures that data used for inference is never used for model training.
Build AI tools on HIPAA-compliant platforms like OpenAI's healthcare offering, but add your own governance layer: audit logs for every inference, explainability requirements for clinical decisions, and automated bias monitoring.
Team Composition and the Scaling of Compliance
Regulated companies fail not just because regulations are hard, but because their organizational structure isn't built to handle them. The right architecture means nothing without the right people to build and maintain it.
The Roles That Matter
- Chief Privacy Officer / Compliance Officer. In healthcare and finance, a dedicated compliance officer is frequently a legal requirement, not an optional hire.
- Regulatory Affairs Engineer. This hybrid role is increasingly essential: someone who understands software architecture well enough to translate a requirement like "audit trails must be immutable" into a specific database choice and logging strategy.
- Security Engineer. The person who implements encryption, access controls, and automated monitoring — and who can explain to an auditor exactly how each one works.
The Scaling Roadmap
- Months 1–3: Regulatory Assessment. Map requirements to your initial architecture. Choose HIPAA-eligible cloud providers. Bring in a part-time consultant if you don't have in-house expertise yet.
- Months 4–9: Compliance Infrastructure. Implement Policy as Code gates. Submit early Q-Submissions to the FDA or begin FinTech state licensing conversations.
- Months 10–18: Certification. Target SOC 2 Type II controls. Establish an internal audit function.
- 18+ Months: Continuous Monitoring. Deploy automated GRC platforms (Vanta, Drata) to track ongoing regulatory changes and flag drift in real time.
The Hidden Accelerator – Engaging Regulators Early
The instinct among technical founders is to treat regulators as obstacles – entities to be managed, not engaged. Early engagement with regulators is one of the highest-ROI moves in regulated domains, yet it's consistently underused.
The FDA Q-Submission
The FDA's Pre-Submission (Pre-Sub) process, part of the broader Q-Submission program, is free, voluntary, and offers written feedback within 70 days of submission. A well-timed Pre-Sub can surface a submission deficiency before it becomes a formal rejection – the kind of rejection that adds a full year to your review cycle. Most companies skip it, assuming they already know what the FDA expects. That assumption is usually wrong.
EU Notified Body Engagement
The MDR transition has put extraordinary pressure on Notified Body capacity. Early 2025 numbers show 51 notified bodies designated under MDR, representing real capacity expansion. Certification timelines haven't budged much: 13-18 months for standard devices and longer for higher-risk classifications. The companies that secured capacity early are moving toward market access, while those waiting risk missing deadlines entirely. Engaging a Notified Body isn't overhead. It's competitive positioning.
The Monolith vs. Microservices Question — It's More Nuanced Than You Think
The standard advice in tech – start monolithic, migrate to microservices at scale – requires careful evaluation in regulated domains. Microservices create compliance complexity: each service boundary introduces a new audit scope, and distributed transactions make unified audit trails significantly harder to maintain. A single database transaction in a monolith becomes a coordinated effort across multiple services, each requiring its own logging, monitoring, and correlation infrastructure.
The pattern gaining traction in regulated platforms is a hybrid architecture. Organizations keep a stable monolithic core for functions where consistency and audit integrity are critical – PHI access, financial transactions, compliance logging. Fast-moving capabilities like AI features, analytics, and UI updates run as microservices at the edge. This matches the actual risk profile: rapid innovation where it matters, locked-down stability where regulations demand it.
Conclusion
Paralysis in regulated industries isn't caused by the existence of regulations. It's caused by the failure to treat them as internal design drivers. The companies moving fastest today — Stripe in payments, Ro in healthcare, Adyen in cross-border finance — are the ones that designed compliance from day one. The result isn't just better audit outcomes. It's a structural competitive advantage: a barrier to entry that, once cleared, is extraordinarily difficult for competitors to replicate quickly.
The barrier is high. But it's the same barrier that becomes, once cleared, a formidable moat. The path forward: treat regulatory requirements as design constraints that shape architecture, not obstacles to route around. Companies that do this build moats their competitors can't cross. Start building systems that make compliance a feature of the product, not a cost center beside it.










%20(1).jpg)
%20(1)%20(1)%20(1).jpg)






.avif)

