DevOps for startups is like a growth accelerator. Done right, it turns engineering into a delivery engine that ships faster, with fewer incidents, and predictable timelines. The global DevOps market was valued at approximately USD 13.16 billion in 2024 and is projected to surge to USD 81.14 billion by 2033, reflecting a striking CAGR of 19.95% during 2025–2033.
The DevOps delivery equation boils down to four measurable metrics:
- Lead time for changes – how fast code moves from commit to production.
- Deployment frequency – how often you can release safely.
- Change failure rate – percentage of releases that cause incidents.
- MTTR (Mean Time to Restore) – how quickly you recover from failures.
When your business goals are tied to technical SLOs (Service Level Objectives), these numbers become direct levers for revenue, customer retention, and operational efficiency.
Shorter lead times mean faster feature releases. Lower failure rates mean happier users and fewer late-night fire drills.
For a clear picture of where you stand, consider a DevOps services audit before making big changes.

DevOps Best Practices, A Startup-Friendly Maturity Model
Startups shouldn’t try to implement enterprise-scale DevOps from day one. Instead, follow a progressive approach that takes you from manual chaos to automated, observable, and secure delivery.
Key maturity stages:
- Level 0 – Manual Chaos
Builds are done on local machines. Testing is ad-hoc. Infrastructure is managed by clicking around in a cloud console. No monitoring or structured security practices exist. - Level 1 – Basic Automation
Builds run in a simple CI tool. Basic unit tests run on pull requests. Some scripts are used to manage infrastructure. Minimal monitoring is in place. - Level 2 – Continuous Delivery
A CI/CD pipeline deploys to staging and production environments with parity. Integration tests are automated. Infrastructure is defined with tools like Terraform or Pulumi. Monitoring and alerting are tied to SLOs. Security scanning starts to be part of the pipeline. - Level 3 – Self-Service & Secure by Default
Developers can deploy without ops bottlenecks. Feature flags control releases. Infrastructure is managed via GitOps. Observability is full-stack (logs, metrics, traces). Security includes SBOMs, signed artifacts, and least privilege IAM.
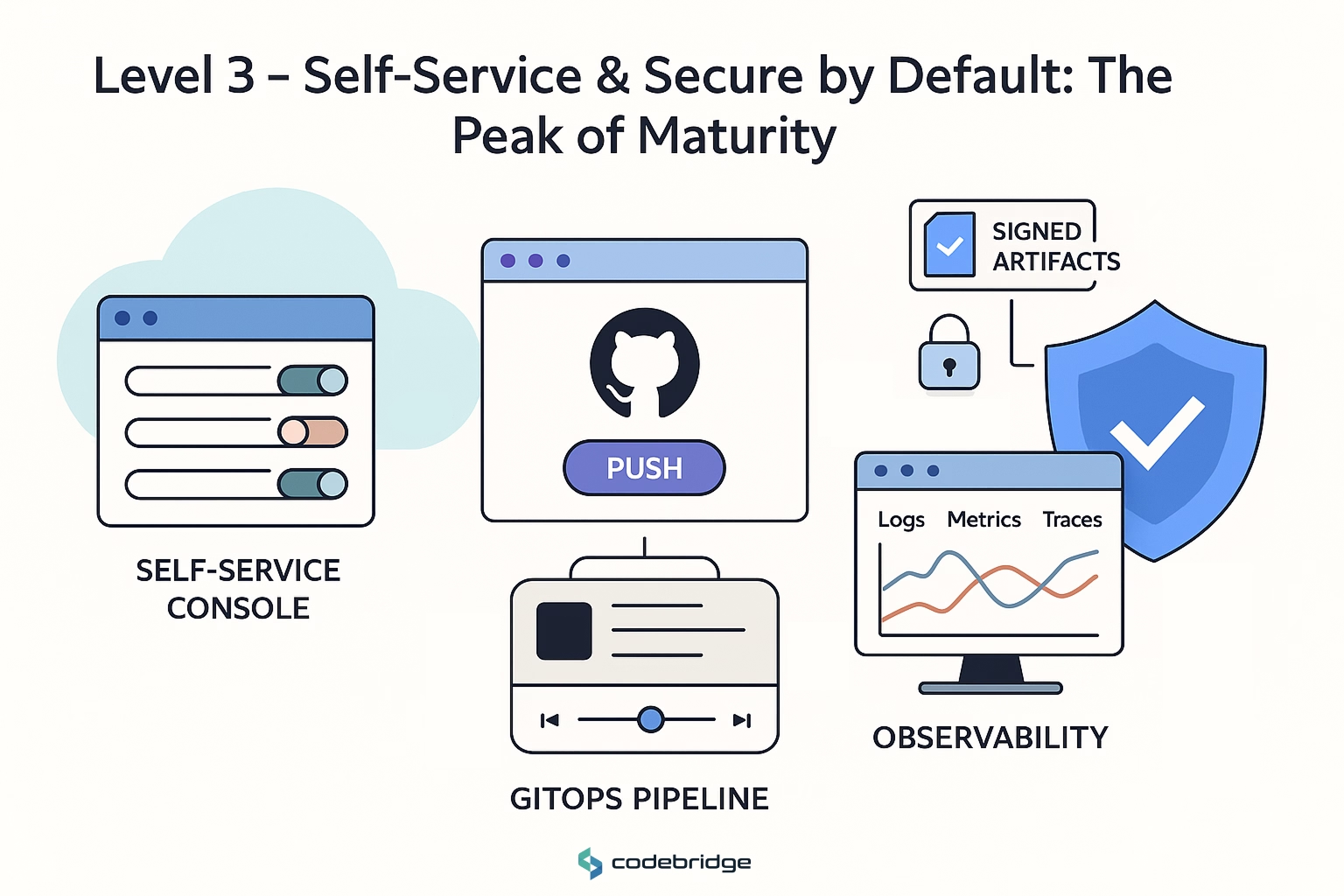
Mapping your current practices to these levels helps set realistic 3–6 month goals.
CI/CD Pipeline, From Commit to Production with Confidence
Your CI/CD pipeline is the heartbeat of DevOps implementation strategies. It’s what turns code commits into customer-facing features, reliably, quickly, and safely.
Core principles for a healthy pipeline:
- Trunk-based development – Keep branches short-lived (1–3 days). Merge changes frequently to avoid long-lived divergence.
- Required checks before merge – Automated builds, tests, linting, and security scans.
- Stages in the pipeline – Build → Test → Package → Deploy → Verify.
- Feature flags – Ship code behind a toggle so you can release safely.
- Progressive delivery – Use blue-green or canary deployments to reduce risk.
- Rollback plan – Be able to revert a change in minutes, not hours.
CI/CD tools worth considering:
- GitHub Actions – Easy for teams already on GitHub; has a large action marketplace.
- GitLab CI – Git, CI/CD, and security scans in one platform.
- CircleCI – Known for speed and parallelism; good for scaling tests.
- Jenkins – Highly customizable and mature, but requires ongoing maintenance.
Recommended release frequency for startups:
- MVP stage: 1–3 deployments per week.
- Growth stage: At least daily deployments.
- Scale stage: Multiple deployments per day or on-demand.
“Level 2” is continuous delivery in practice. The team deploys regularly to a staging environment that mirrors production. Infrastructure is managed through Infrastructure as Code tools like Terraform or Pulumi. Automated integration tests run alongside unit tests. Monitoring covers not just uptime but also key performance metrics, and security scanning
Infrastructure as Code & Cloud Foundations
For startups aiming to scale without drowning in manual infrastructure work, Infrastructure as Code (IaC) is non-negotiable. It makes environments reproducible, scalable, and less error-prone.
Core principles of modern IaC for startups:
- Environment parity – Staging and production should be nearly identical to prevent “it works on staging” surprises.
- Version control for infrastructure – All infrastructure definitions live in Git, with peer reviews before changes are applied.
- Policy as code – Security and compliance rules embedded into the provisioning process (e.g., no public S3 buckets, least privilege IAM).
- Automated provisioning – Onboarding a new environment should be a command, not a two-day manual process.
GitOps workflow basics:
- Deploy changes via Git merges, not by running scripts manually.
- Use pull-based deployments so clusters and environments stay in sync automatically.
- Monitor for configuration drift and revert changes if necessary.
Popular IaC tool options and their startup fit:
- Terraform – Mature, multi-cloud support, huge provider ecosystem, declarative syntax. Great for most startups.
- Pulumi – Lets you define infrastructure in real programming languages (TypeScript, Python, Go). Ideal for teams that want to reuse existing dev skills.
- CloudFormation – AWS-native, tight integration, but less portable to other clouds. Good for AWS-only shops.

Containers & Kubernetes for Startups
Containers can speed up deployments, improve consistency, and enable portability. But Kubernetes is not always the starting point for a small team; adoption should be driven by actual scaling needs.
When to adopt containers:

- You need consistent environments from local to production.
- Your app needs isolation between services without full VMs.
- You plan to scale beyond a single monolithic app or add microservices.
Startup-friendly container orchestration options:
- Amazon ECS – Simple, AWS-managed, good for small teams.
- AWS App Runner – Abstracts away most container complexity, great for MVPs.
- Google Cloud Run – Similar to App Runner, scales from zero.
- EKS/GKE – Fully managed Kubernetes clusters, better for teams with in-house ops skills.
Best practices for container/K8s use in startups:
- Use ephemeral environments for testing every PR.
- Set resource limits to prevent noisy neighbor problems.
- Enable horizontal pod autoscaling (HPA) early to handle traffic spikes.
- Manage manifests with Helm or Kustomize to keep them DRY.
SRE & Observability, Reliability Without Slowing Down
Borrowing Site Reliability Engineering (SRE) practices helps startups avoid chaos as they grow, without making processes so heavy they slow innovation.
Key practices to implement:
- SLOs (Service Level Objectives) – Define measurable reliability goals (e.g., “99.9% availability for checkout API”).
- Error budgets – Accept a small amount of failure to ship features faster, but pause releases if reliability drops below the target.
- Full observability stack – Logs, metrics, and traces collected from all environments.
- Synthetic checks – Simulate user journeys to catch issues before customers do.
- Incident runbooks – Step-by-step guides for handling known failure scenarios.
Metrics to monitor in your DevOps reporting:
- Lead time for changes.
- Deployment frequency.
- Change failure rate.
- MTTR (Mean Time to Restore).

DevSecOps, Bake Security into the Pipeline
For growing startups, security cannot be an afterthought. DevSecOps embeds it into every stage of delivery, preventing vulnerabilities from shipping to production.
Core DevSecOps practices to adopt early:
- Automated security scans in CI/CD
- SAST (Static Application Security Testing) for code vulnerabilities before deployment.
- DAST (Dynamic Application Security Testing) for runtime behavior.
- SCA (Software Composition Analysis) to check third-party dependencies.
- Secrets management
- Store keys, tokens, and passwords in a vault (e.g., HashiCorp Vault, AWS Secrets Manager).
- Automate key rotation.
- Enforce least privilege IAM policies.
- Supply chain security
- Sign and verify all build artifacts.
- Maintain a Software Bill of Materials (SBOM).
- Use provenance metadata to ensure code comes from trusted sources.
Cost & Efficiency, FinOps for DevOps Leaders
As infrastructure grows, cloud bills can spiral out of control. FinOps brings financial accountability into engineering decisions.
FinOps tactics for startups:
- Unit cost dashboards
- Track cost per request, per active user, or per transaction.
- Set budget alerts tied to usage spikes.
- Optimize resource allocation
- Right-size instances and containers based on actual usage.
- Move cold data to cheaper storage tiers.
- Use CDN caching to reduce egress charges.
- Commit coverage based on SLOs, not guesses
- Use AWS Savings Plans or Reserved Instances only for workloads with predictable demand.
- Avoid overcommitting on resources just to chase discounts.
Org & Platform, From Ad-Hoc Ops to Platform Engineering
As teams scale, platform engineering becomes a force multiplier. Instead of every team reinventing pipelines, create shared, self-service infrastructure.
Key building blocks of an internal platform:
- Golden paths – Pre-approved, documented ways to build, test, and deploy services without friction.
- Internal developer portal – One place for service docs, templates, credentials, and monitoring dashboards.
- Self-service environments – Developers can spin up and tear down test environments without ops tickets.
- SLAs for the platform – Commit to uptime, support response times, and deployment reliability for internal tools.
0–30 Days: Foundation
- Assess your current DevOps maturity level.
- Select and configure a CI/CD tool.
- Define SLOs and begin tracking DORA metrics.
- Bootstrap Infrastructure as Code for core environments.
31–60 Days: Expansion
- Implement GitOps workflows for deployments.
- Add observability: logs, metrics, traces, and uptime checks.
- Introduce feature flags for safer releases.
- Enable automated security scans in CI/CD.
61–90 Days: Optimization
- Containerize workloads where it makes sense.
- Launch cost dashboards and budget alerts.
- Create “golden path” templates for new services.
- Review and refine SLOs based on observed performance.
Toolchains That Work (Opinionated but Flexible)
Instead of chasing the latest shiny tool, build a cohesive, maintainable stack:
- Starter stage – GitHub Actions or GitLab CI, Terraform for IaC, lightweight monitoring (Grafana/Prometheus), container registry.
- Growth stage – GitOps (ArgoCD or Flux), Kubernetes (managed service like EKS/GKE/AKS), full observability suite (Datadog, New Relic), centralized secrets vault.
- Scale stage – Dedicated platform team, internal developer portal (Backstage), advanced security tooling (Snyk, Trivy), automated cost governance (CloudHealth).
Common Pitfalls & How to Avoid Them
- Over-automating too early – Start with what’s critical for delivery speed and reliability before scaling automation everywhere.
- Platform sprawl – Avoid adopting multiple overlapping tools without clear ownership.
- Skipping incident reviews – Every outage should feed back into improved processes and tooling.
- No rollback plan – Canary and blue-green deployments are useless without tested rollbacks.
- Security bolted on late – Integrate scanning and secrets management from the start.
- Runaway cloud costs – Pair FinOps practices with engineering KPIs.
Final Conclusion
A strong DevOps foundation can shrink delivery times, improve reliability, and scale your startup without chaos.
Our team helps startups assess their current maturity, choose the right tools, and implement best practices tailored to their stage of growth. Book a free consultation to start your 30/60/90-day rollout today.
FAQ
What is DevOps implementation?
DevOps implementation is the process of integrating development and operations teams to improve collaboration, automate workflows, and accelerate software delivery. By adopting DevOps practices, startups can achieve faster releases, fewer errors, and better alignment between business goals and technical execution.
Why is DevOps implementation important for growing startups?
For growing startups, DevOps implementation helps streamline the entire product lifecycle. It reduces bottlenecks between developers and operations, shortens deployment cycles, and ensures quicker feedback loops. This agility allows startups to innovate faster and scale efficiently without compromising product stability.
What are the key steps in successful DevOps implementation?
The essential steps of DevOps implementation include:
- Assessing current workflows and identifying gaps.
- Building a culture of collaboration between dev and ops teams.
- Automating CI/CD pipelines for faster code delivery.
- Implementing monitoring and feedback systems.
- Iterating continuously to refine processes.
These steps help startups transition smoothly to a DevOps-driven model.
Which tools are best for DevOps implementation in startups?
Top tools for DevOps implementation include:
- CI/CD: Jenkins, GitHub Actions, GitLab CI
- Containerization: Docker, Kubernetes
- Monitoring: Prometheus, Grafana
- Cloud: AWS, Azure, Google Cloud
Using these tools enables automation, scalability, and real-time visibility, key factors for startup growth.
What challenges do startups face during DevOps implementation?
Common challenges in DevOps implementation include lack of skilled engineers, resistance to process change, and insufficient automation. Startups can overcome these issues by starting small, focusing on cultural transformation, and using managed DevOps services to fill skill gaps during the transition.
How does DevOps implementation impact product quality and delivery speed?
When executed effectively, DevOps implementation leads to higher product quality and faster delivery. Continuous integration ensures early detection of bugs, while automated testing and deployment reduce downtime. This enables startups to release updates more frequently and respond to user feedback in real time.