Cloud security threats have vaulted to the forefront of executive agendas as adversaries exploit misconfigurations, supply chain vulnerabilities, and unseen environments.
Myroslav Budzanivskyi, Founder and CTO at Codebridge Technology, Inc., with over 15 years in DevOps Services and cybersecurity, emphasizes that today’s highest risks rarely involve brute-force front-door hacks. Instead, attackers infiltrate through dependencies, configuration drift, and unattended workloads.
This article presents a comprehensive SERP analysis and content framework, spanning threat landscapes, strategic configurations, deployment contexts, application protection, compliance, and future innovations, to secure top-10 rankings and guide practitioners to build resilient defenses.

What Are the Most Pressing Cloud Security Threats Today?
The modern cloud ecosystem faces an array of sophisticated cloud security threats:
- Data breaches exploiting stolen credentials, over-privileged IAM roles, and publicly accessible storage buckets.
- Misconfigurations in network ACLs, security groups, and container orchestration settings leading to unintended exposure.
- IAM failures such as identity sprawl, insufficient multi-factor enforcement, and excessive trust relationships.
Key 2026 metrics illustrate the urgency:
This cost burden and attack velocity make cloud security threats a boardroom priority, demanding content that unpacks root causes and prescriptive mitigations.
How Do Cloud Computing Security Threats Differ from Traditional Server Risks?
Unlike static on-premise servers, cloud platforms introduce dynamic risk vectors:
Understanding this shift is crucial; traditional perimeter defenses falter against cloud computing security threats and the shared responsibility model, necessitating continuous, context-aware monitoring.
Which AI Security Monitoring Risks Are Emerging in the Cloud?
AI-driven security tools deliver advanced detection but introduce new hazards:
- Model poisoning: Malicious data injected during ML training skews threat classification.
- Data poisoning: Corrupted telemetry hides real attack patterns.
- Explainability gaps: Legacy SIEM/CSPM solutions lack context to interpret AI alerts, causing blind spots.

How Does a Cloud Security Strategy Mitigate Misconfiguration Risks?
A resilient cloud security strategy fuses zero-trust principles, CSPM tools, and automated drift detection:
- Zero-Trust Architecture: Authenticate and authorize every request with least-privilege enforcement.
- CSPM Integration: Continuously benchmark resources against CIS, NIST, and provider standards, automating remediation of drift. (Google Cloud Security Foundations Guide)
- Automated IaC Drift Workflows: Leverage policy-as-code in Terraform, ARM, or CloudFormation pipelines to detect and revert unauthorized changes.
What Are the Best Practices in Cloud Security Checklist for DevSecOps Teams?
An effective cloud security checklist for DevSecOps spans:
Configuration Hardening
Enforce encrypted storage (AES-256), secure TLS profiles, and secure boot on VMs.
Policy as Code
Embed security guardrails in IaC templates to block non-compliant resources. (ENISA Cloud Security Risk Assessment)
Continuous Compliance
Integrate security checks into CI/CD pipelines, triggering fail-fast alerts on violations.
Secrets Management
Store and rotate credentials in vault services; use ephemeral tokens.
Runtime Protection
Deploy RASP, container security agents, and network policies with service-mesh controls.

Expert Insights
Myroslav Budzanivskyi, Founder and CTO at Codebridge Technology, Inc., has more than 15 years of experience in DevOps and cybersecurity.
After working with dozens of clients this year, I've noticed something interesting: the biggest security threats in 2025 aren't coming from hackers trying to break down your front door. Instead, they're sneaking in through your supply chain, exploiting configuration mistakes, and taking advantage of environments that nobody's really watching.
Here's what Myroslav Budzanivskyi telling teams to focus on:
Stop ignoring your dependencies
Attackers have gotten smarter. Instead of trying to hack your app directly, they're going after your Docker images, Terraform modules, and third-party libraries. I've seen too many breaches that started with a compromised NPM package. The fix? Start signing your images and keep track of every component in your supply chain with an SBOM (Software Bill of Materials). It's boring work, but it'll save you later.
Make everything temporary
This one's a game-changer. Create secrets, user accounts, and containers only when you need them, then destroy them immediately after use. We call this "Just-In-Time" access. It sounds extreme, but think about it – attackers can't compromise what doesn't exist. The shorter something lives, the smaller the window for attack.
AI monitoring isn't magic
Everyone's talking about AI-powered security monitoring, and yes, it can help spot weird behavior in your systems. But here's the thing – it's not plug-and-play. You'll spend weeks training it on your specific logs and adjusting thresholds to cut down on false alarms. Don't expect it to work perfectly out of the box.
Watch what's leaving, not just what's coming in
Most companies obsess over who's getting into their systems but ignore what's going out. Big mistake. I've seen more data breaches caused by unrestricted outbound traffic than sophisticated intrusions. Set clear rules about what data can leave your environment and actually monitor those flows, especially from production.
Treat shared hosting like the Wild West
If you're stuck on shared hosting, assume it's already compromised. Add an external web application firewall, use a separate secrets manager, and send your logs somewhere else for monitoring. Layer your defenses because you can't trust the infrastructure.
Where to start
If you're just getting into security, don't jump straight to the advanced stuff. Get your basics right first: keep everything patched, enable multi-factor authentication everywhere, and use secure defaults. Build that foundation, then add the fancy stuff later. For the experienced folks reading this, 2025 is about three things: getting rid of long-lived credentials, controlling what leaves your network, and actually testing your incident response with realistic drills. The threat landscape changes faster than our defenses these days, so your team better be ready to adapt.
Why Is Cloud Security Trends Analysis Vital for Future-Proofing?
Staying abreast of cloud security trends arms organizations to:
- Navigate multi-cloud adoption, addressing provider-specific misconfigurations.
- Harness predictive analytics to correlate logs, metrics, and traces for early threat warnings.
- Deploy confidential computing and hardware-root-of-trust solutions against APTs.
Regular cloud security trends reports engage audiences and reinforce thought leadership, driving sustained SERP authority.
What Unique Challenges Exist for Security in Private Cloud Environments?
Private clouds introduce:
- Isolation gaps without standardized network micro-segmentation.
- Patch management lags for bespoke virtualization and hypervisor platforms. (Microsoft Azure Security Documentation)
- Insider threats, given extensive admin privileges.
Case Study: A financial institution suffered a breach due to outdated hypervisor firmware. Root cause: neglected patch cycles and missing hardware attestation.
How Can Enterprises Strengthen Security Private Cloud Architectures?
Effective controls for security private cloud include:
- Network micro-segmentation with software-defined firewalls to isolate tenant workloads.
- Hardware root of trust via TPM modules to verify hypervisor integrity at boot.
- SIEM integration unifying logs across on-prem and private cloud infrastructures.
What Does Cloud vs Server Security Mean for Hybrid Deployments?
Hybrid setups demand:
- Unified policy enforcement across CSPM, EDR, and NAC solutions.
- Cost-benefit analysis of cloud-native controls (serverless WAF) versus legacy appliances.
- Operational orchestration combining DevSecOps and traditional security skillsets.
This cloud vs server security narrative clarifies hybrid complexities and captures both cloud- and on-prem-focused audiences.
How Should Organizations Address Application Security in Cloud Computing?
Robust application security in cloud computing follows a layered model:
- Shift-left security: SAST, DAST, and threat modeling early in the SDLC.
- Container image scanning: Automated vulnerability checks before deployment.
- Runtime defense: Service-mesh mTLS, sidecar proxies, and WAF configuration at the API gateway.
Which Techniques Enhance Application Security in Cloud Workloads?
Advanced defenses include:
- Service-mesh mTLS for mutual authentication and encryption.
- Code signing pipelines to verify artifact integrity at deployment.
- Secrets management with vaults, dynamic credentials, and short-lived tokens.
Real-World Breach: The Optus API breach stemmed from missing authentication checks. Remediation included enforcing OAuth scopes, rotating keys, and fine-tuning WAF rules.
What Role Does Cloud Compliance & Governance Play in Risk Reduction?
A mature cloud compliance & governance framework ensures:
- Standards mapping: Aligning configurations to GDPR, HIPAA, PCI DSS.
- Audit automation: Continuous evidence collection via API integrations.
- Policy-embedded pipelines: Fail-fast gates that block non-compliant deployments.
How Will Cloud Security Threats 2025 Evolve with Quantum Computing?
Quantum advances threaten existing cryptography:
- Post-quantum cryptography: Lattice-based, hash-based, and code-based schemes for quantum-resilient key exchange.
- Quantum key distribution and hybrid models to secure data in transit and at rest.
What Opportunities Exist for Multi-Cloud Security Orchestration?
Multi-cloud environments drive orchestration innovations:
- Centralized policy engines (OPA, Istio Gatekeeper) for consistent guardrails.
- Cross-provider SIEM solutions aggregating telemetry for unified alerting.
- Ecosystem partnerships offering plug-and-play modules for vulnerability management and compliance.
How Can Organizations Build a Holistic Cloud Security Strategy Today?
A strategic roadmap includes:
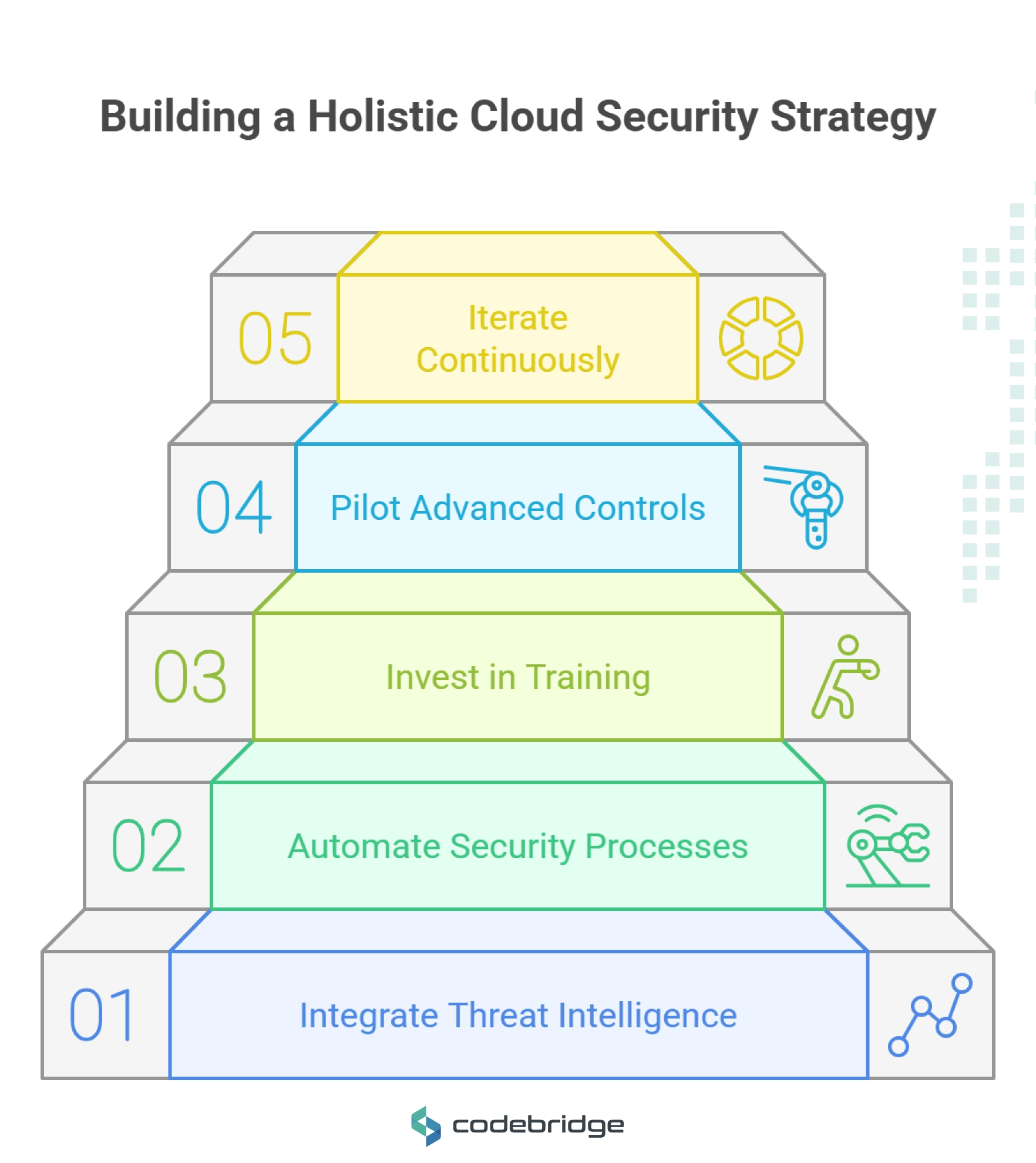
- Integrate threat intelligence into SIEM and CSPM for contextual alerts.
- Automate drift detection, compliance checks, and ai security monitoring to close gaps.
- Invest in training, from just-in-time access to quantum-resilient cryptography.
- Pilot advanced controls, confidential computing, hardware root of trust, predictive analytics, in non-prod.
- Iterate continuously, tracking MTTD and MTTR metrics to refine processes.
Begin with a security assessment to uncover critical gaps, launch a pilot for automated compliance and detection, and foster a culture of vigilance and adaptability to defend against evolving cloud security threats.
Partner with Codebridge to turn these strategies into action and build a resilient, AI-driven security foundation for your organization.
FAQ
What are the essential items on a “cloud security checklist”?
A complete cloud security checklist should cover configuration hardening, policy-as-code enforcement, continuous compliance, secrets management, and runtime protection. Key actions include encrypting storage volumes, embedding CIS/NIST policies in Terraform or ARM templates, integrating security gates in CI/CD pipelines, rotating credentials with a vault solution, and deploying service-mesh mTLS for live threat mitigation.
Why is analyzing “cloud security trends” critical for my organization?
Tracking cloud security trends helps you anticipate emerging risks, such as multi-cloud misconfigurations, confidential computing advancements, and predictive analytics capabilities, so you can align security investments with future threat landscapes and maintain a proactive defense posture.
What unique challenges affect “security in private cloud” environments?
In security in private cloud setups, you face tenant isolation gaps, bespoke hypervisor patch management, and elevated insider threat potential. Implement software-defined micro-segmentation, hardware root of trust (TPM), and unified SIEM integration to address these specialized risks.
How can I strengthen my “security private cloud” architecture?
To enhance security private cloud, enforce network micro-segmentation with virtual firewalls, verify hypervisor integrity via TPM modules, and correlate logs across on-premises and private cloud workloads within your SIEM for comprehensive visibility and incident response.
What distinguishes “cloud computing security threats” from traditional on-prem risks?
Cloud computing security threats revolve around dynamic APIs, ephemeral workloads (containers/serverless), and the shared responsibility model. Unlike on-prem attacks focused on physical or network breaches, cloud threats exploit misconfigurations, IAM failures, and orchestration-layer vulnerabilities.
Which “cloud security threats” pose the greatest risk in 2026?
Top cloud security threats include data breaches via misconfigured storage, identity and access mismanagement, supply-chain compromise of Docker images and Terraform modules, and emerging AI/ML model or data poisoning attacks that evade conventional detection.